TryHackMe: Nessus Room Writeup
Learn how to set up and use Nessus, a popular vulnerability scanner.
Task 3
What is the name of the button which is used to launch a scan?

New Scan
What side menu option allows us to create custom templates?

Policies
What menu allows us to change plugin properties such as hiding them or changing their severity?
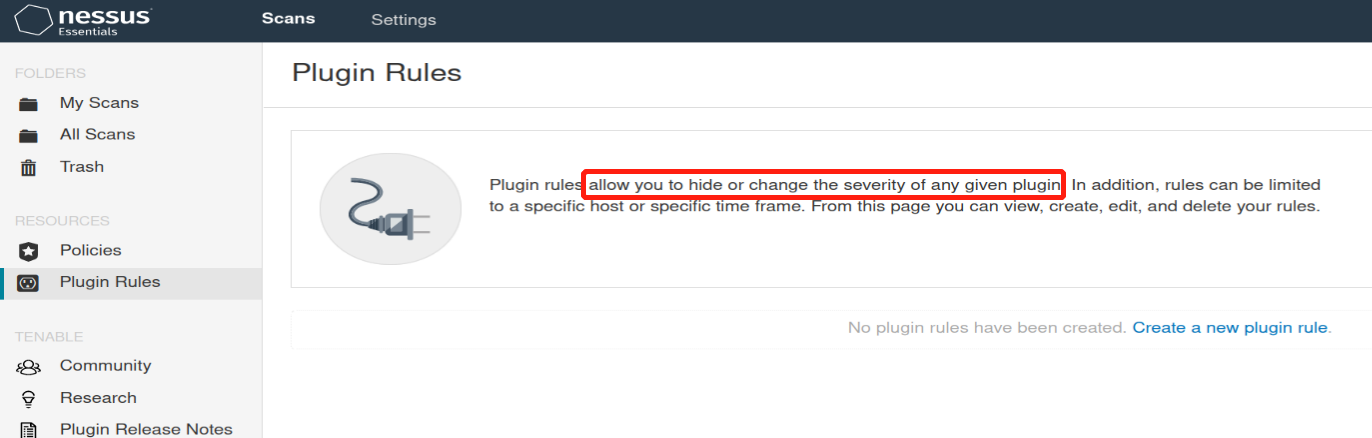
Plugin Rules
In the ‘Scan Templates’ section after clicking on ‘New Scan’, what scan allows us to see simply what hosts are alive?
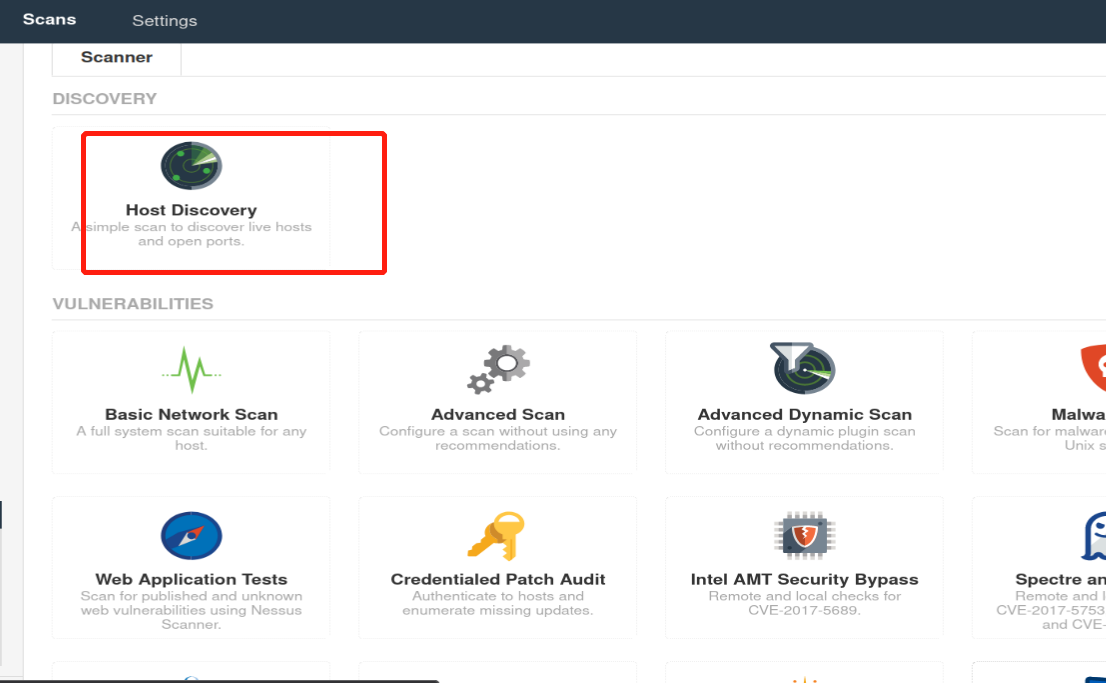
Host Discovery
One of the most useful scan types, which is considered to be ‘suitable for any host’?

Basic Network Scan
What scan allows you to ‘Authenticate to hosts and enumerate missing updates’?

Credentialed Patch Audit
What scan is specifically used for scanning Web Applications?

Web Application Tests
Task 4
Create a new ‘Basic Network Scan’ targeting the deployed VM. What option can we set under ‘BASIC’ (on the left) to set a time for this scan to run? This can be very useful when network congestion is an issue.
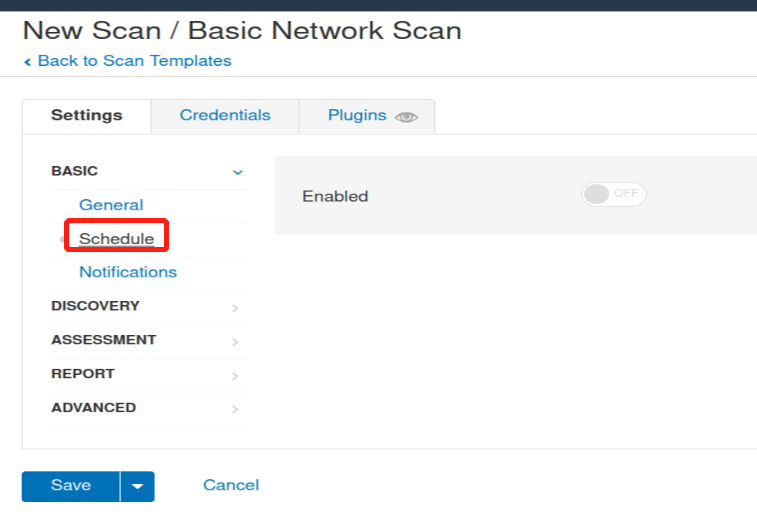
Schedule
Under ‘DISCOVERY’ (on the left) set the ‘Scan Type’ to cover ports 1-65535. What is this type called?
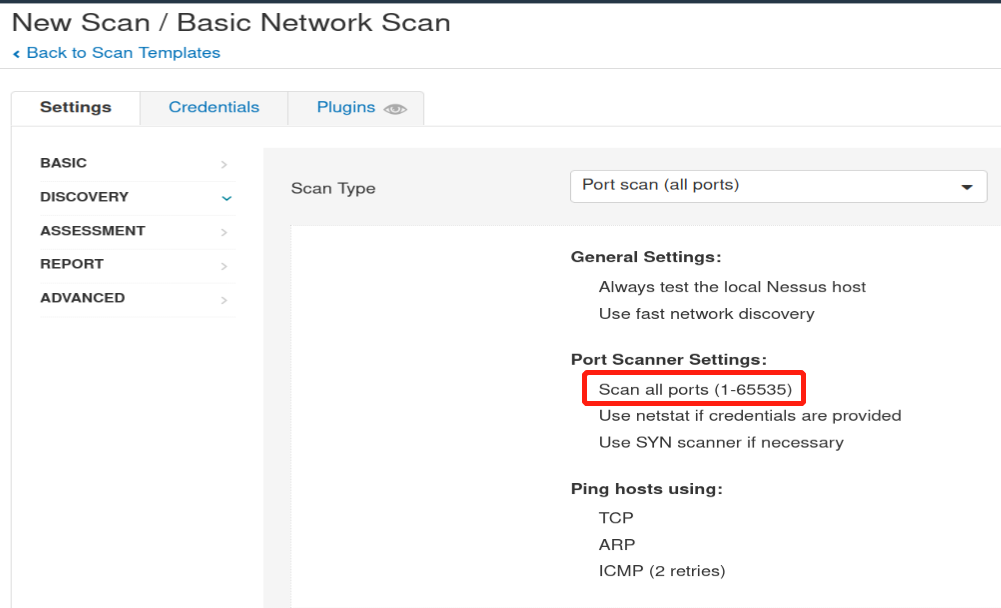
Port scan (all ports)
What ‘Scan Type’ can we change to under ‘ADVANCED’ for lower bandwidth connection?
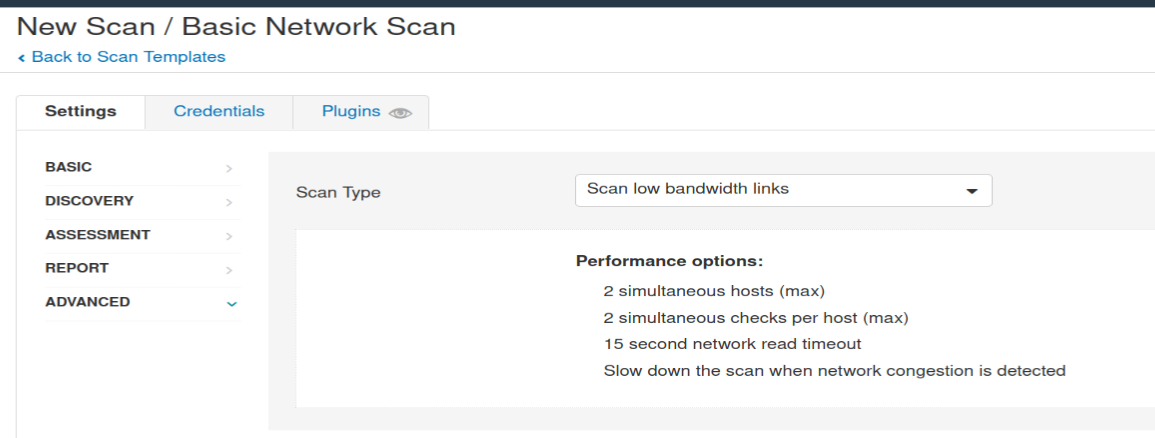
Scan low bandwidth links
After the scan completes, which ‘Vulnerability’ in the ‘Port scanners’ family can we view the details of to see the open ports on this host?
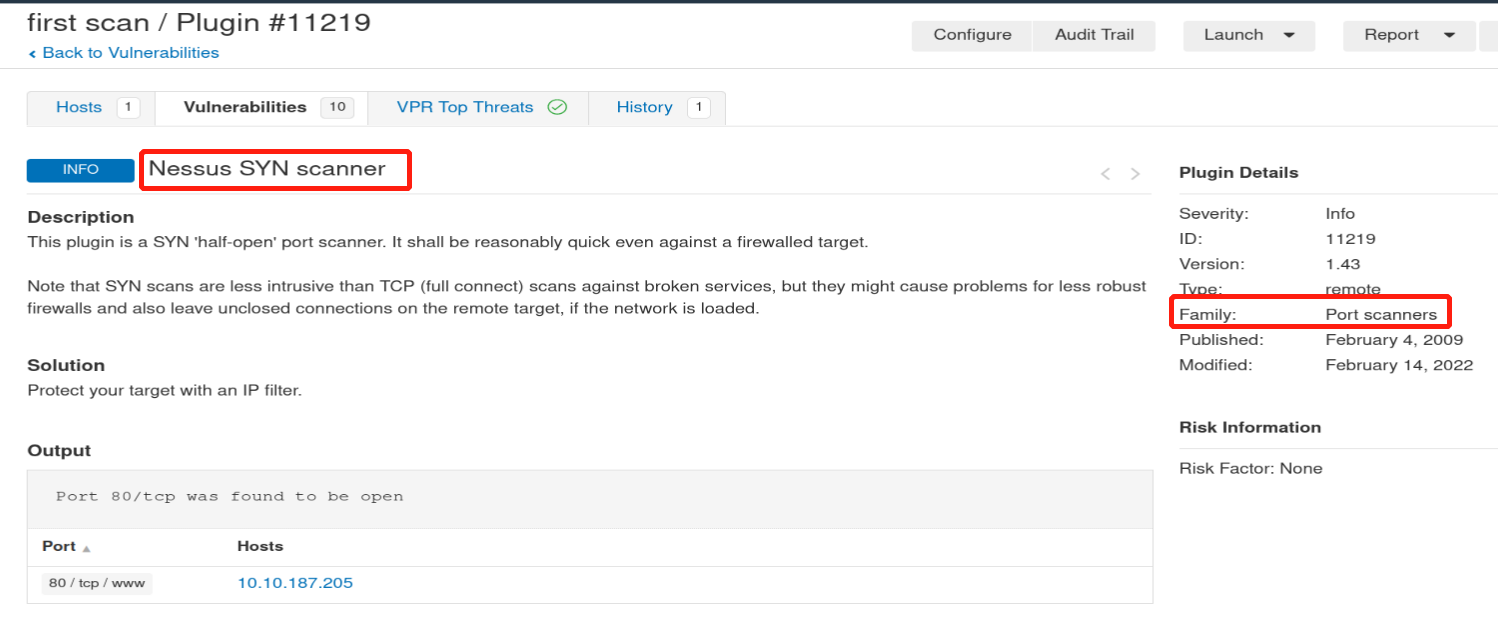
Nessus SYN scanner
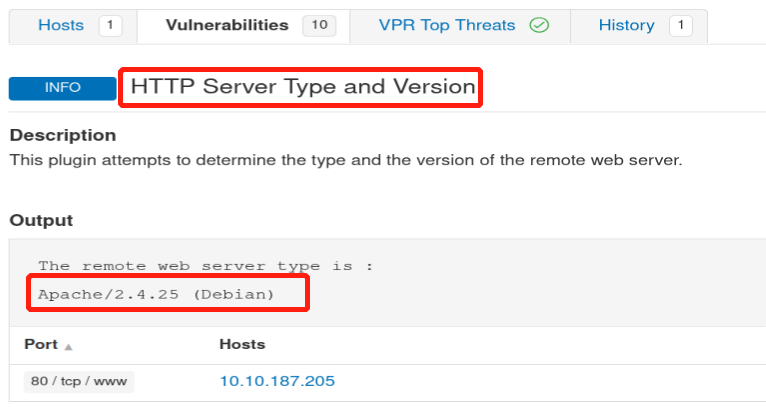
What Apache HTTP Server Version is reported by Nessus?
There might be some confusion here that I must mention.
In the below picture we see the apache version is 2.4.25, but that is not the correct answer.
You need to wait until the scan finishes or the vulerability named ‘Apache HTTP Server Version’ showes up in the panel.
 And here below is the true answer:
And here below is the true answer:
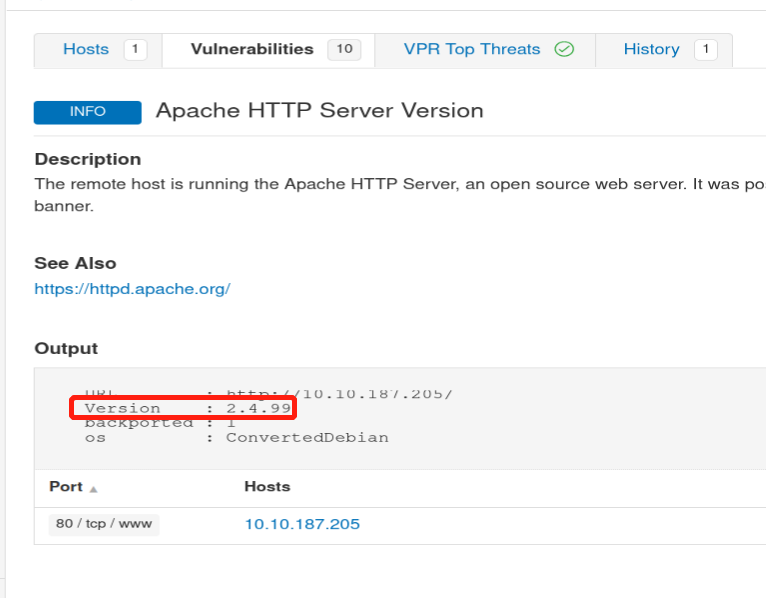
2.4.99
Task 5
What is the plugin id of the plugin that determines the HTTP server type and version?

10107
What authentication page is discovered by the scanner that transmits credentials in cleartext?

login.php
What is the file extension of the config backup?
To find the config backup you can look up the vulnerabilities including information about some URL paths, and then visit those paths to check if there’re any backup files available.
But here there’s also a medium severity vulnerability showing up, so you can just open it and see the result:
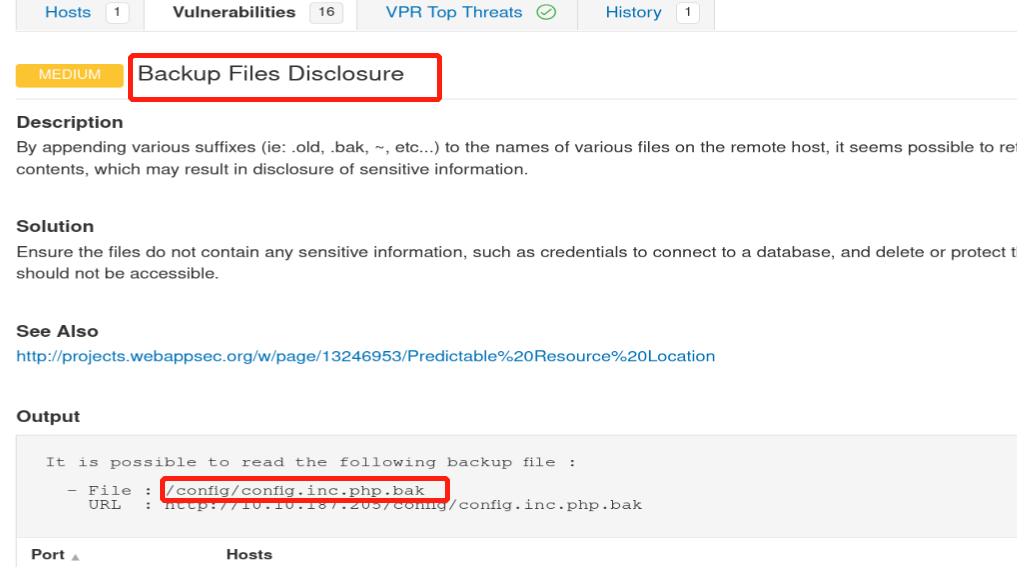
.bak
Which directory contains example documents? (This will be in a php directory)
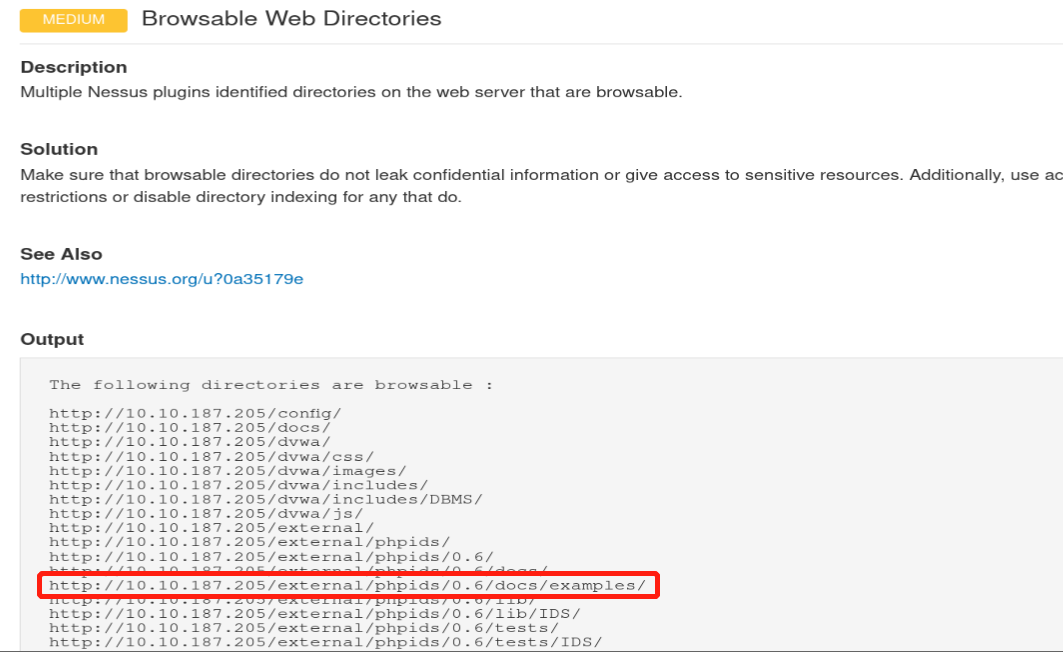
/external/phpids/0.6/docs/examples/
What vulnerability is this application susceptible to that is associated with X-Frame-Options?
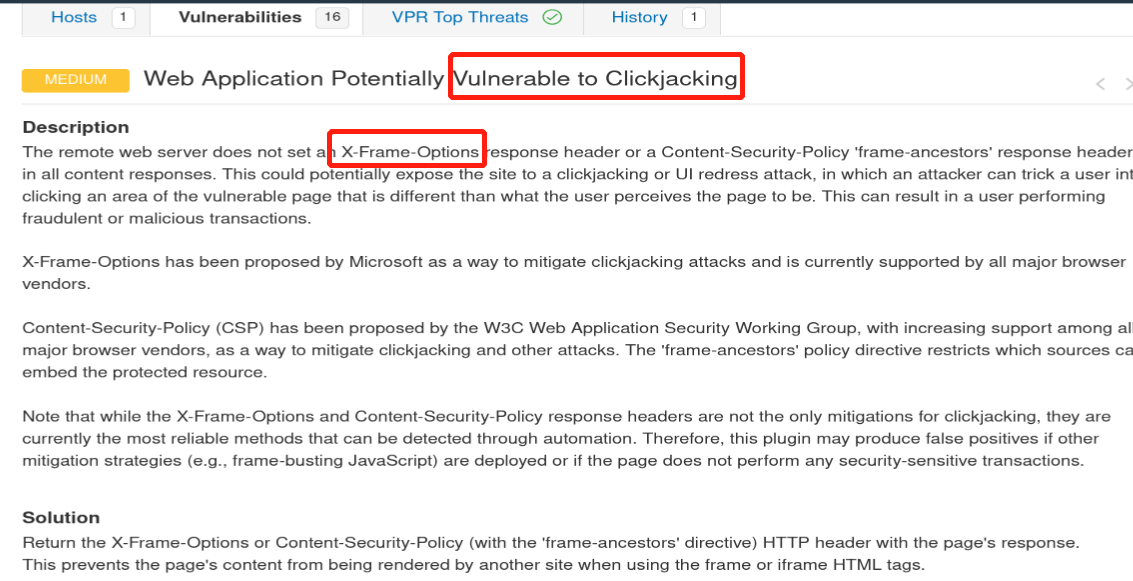
原创文章转载请注明出处: Nessus Room WriteupClickjacking